Introduction
Pulsar is a powerful, blazing fast security observability framework designed specifically to address the challenges of embedded security of Linux devices.
Powered by eBPF and written in Rust, Pulsar is lightweight, safe by design and gives you full access to your devices security.
Architecture
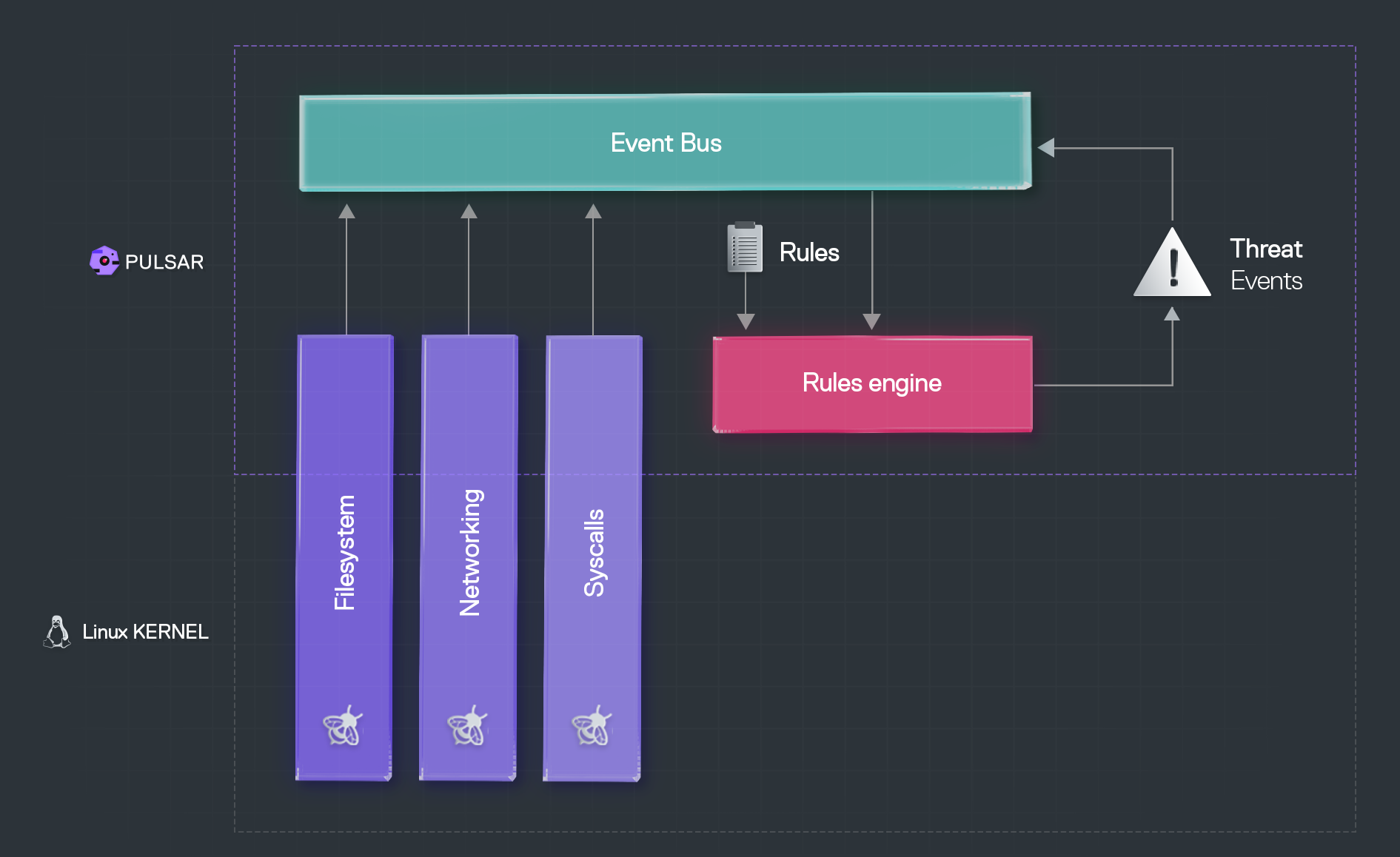
At its core, Pulsar is an event-driven framework for monitoring the activity of Linux devices. Pulsar allows you to collect runtime information about the system from the Linux kernel through its modules, enrich and transform this information into events and publish the events on a shared event bus.
Through the Pulsar rules engine, you can write and apply any rule to generate alerts when undesired system behaviour occurs (e.g. accessing certain areas of the filesystem).
Any event that matches one of the rules enforced by the rules engine is known as a threat event.
Features
In general, the information collected by default from the kernel by the Pulsar modules through the eBPF probes can be grouped into 4 distinct categories:
File I/O: I/O operations on disk and memory.
Network: data from the network stack.
Processes: processes information, including file execution and file opening.
System Activity: device activity, including system calls.
Pulsar modular design makes it easy to adapt the core architecture to diverse use cases. In fact, if there isn't yet a module that does what you need, you can simply create one yourself and load it; all the events collected by the new module will be available on the event bus for further processing and threat analysis.
Next Steps
If what you've heard so far sounds interesting, check out the Getting Started section of the documentation to start using Pulsar. Or, follow along to dive deeper into the main Concepts behind Pulsar's design.